Access token microsoft
Upgrade to Microsoft Edge to take advantage of the latest features, security updates, and technical support. Access tokens enable clients to securely call protected web APIs. Web APIs use access tokens to perform authentication and authorization. Per the OAuth specification, access tokens are opaque strings access token microsoft a set format.
Upgrade to Microsoft Edge to take advantage of the latest features, security updates, and technical support. It's protected by the Microsoft identity platform, which uses OAuth access tokens to verify that an app is authorized to call Microsoft Graph. This article provides an overview of the Microsoft identity platform, access tokens, and how your app can get access tokens. For more information about the Microsoft identity platform, see What is the Microsoft identity platform? If you know how to integrate an app with the Microsoft identity platform to get tokens, see the Microsoft identity platform code samples for information and samples specific to Microsoft Graph. Before your app can get an access token from the Microsoft identity platform, it must be registered in the Microsoft Entra admin center. Registration integrates your app with the Microsoft identity platform and establishes the information that it uses to get tokens, including:.
Access token microsoft
Upgrade to Microsoft Edge to take advantage of the latest features, security updates, and technical support. To call a resource server, the HTTP request must include an access token. This article shows you how to request an access token for a web application and web API. This scenario is common in clients that have a web API back end, which in turn calls a another service. Scopes provide a way to manage permissions to protected resources. When an access token is requested, the client application needs to specify the desired permissions in the scope parameter of the request. Scopes are used by the web API to implement scope-based access control. For example, users of the web API could have both read and write access, or users of the web API might have only read access. To acquire multiple permissions in the same request, you can add multiple entries in the single scope parameter of the request, separated by spaces. If you request more scopes than what is granted for your client application, the call succeeds if at least one permission is granted. The scp claim in the resulting access token is populated with only the permissions that were successfully granted. The OpenID Connect standard specifies several special scope values. The following scopes represent the permission to access the user's profile:.
Hybrid OIDC flow. Not all applications should validate tokens. Both the client and the user must be authorized to make the request.
Upgrade to Microsoft Edge to take advantage of the latest features, security updates, and technical support. This is because each Microsoft Entra ID token is short-lived, typically expiring within one hour. After this time, you must manually generate a replacement Microsoft Entra ID token. Instead, use one of the participating tools or SDKs that implement the Databricks client unified authentication standard. This article describes basic usage of the MSAL library and required user inputs, with Python examples.
Upgrade to Microsoft Edge to take advantage of the latest features, security updates, and technical support. JWTs contain the following pieces:. Claims are present only if a value exists to fill it. An application shouldn't take a dependency on a claim being present. The access token will always contain sufficient claims for access evaluation. The Microsoft identity platform uses some claims to help secure tokens for reuse. The description of Opaque marks these claims as not being for public consumption.
Access token microsoft
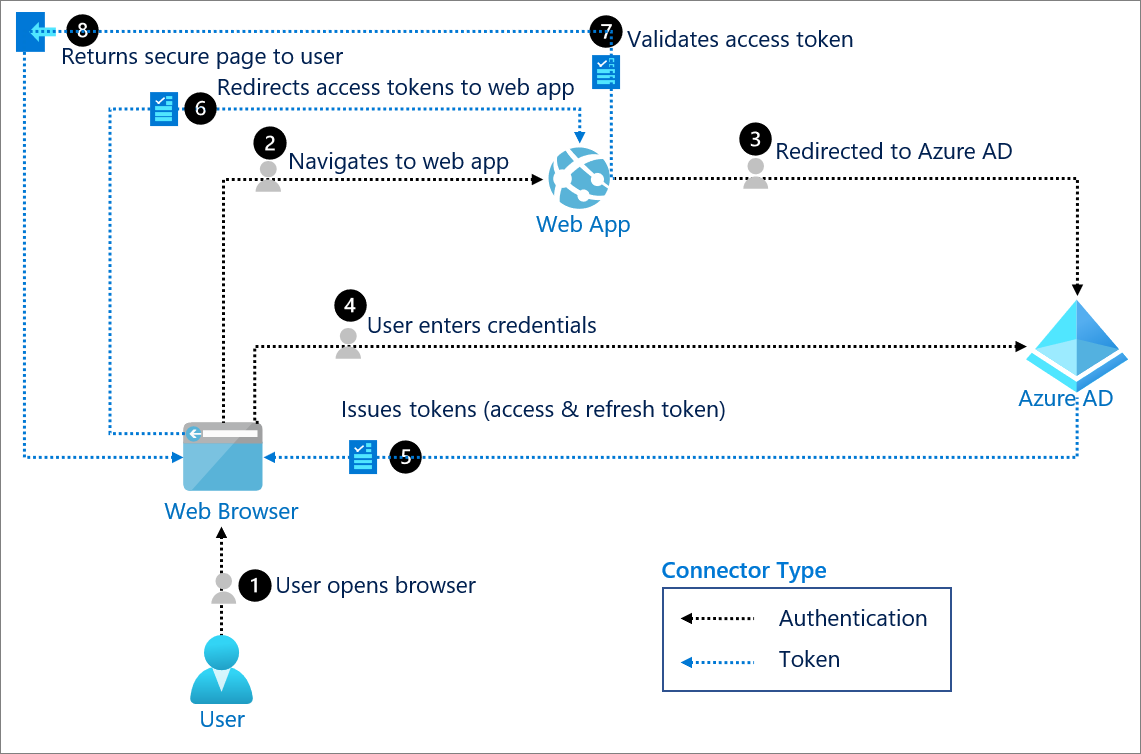
Upgrade to Microsoft Edge to take advantage of the latest features, security updates, and technical support. A centralized identity provider is especially useful for apps that have worldwide users who don't necessarily sign in from the enterprise's network. The Microsoft identity platform authenticates users and provides security tokens, such as access tokens, refresh tokens, and ID tokens. Security tokens allow a client application to access protected resources on a resource server. Many enterprise applications use SAML to authenticate users. It's up to the application for which the token was generated, the web app that signed in the user, or the web API being called to validate the token. The authorization server signs the token with a private key. The authorization server publishes the corresponding public key. To validate a token, the app verifies the signature by using the authorization server public key to validate that the signature was created using the private key. For more information, check out the Secure applications and APIs by validating claims article.
Link loz botw
Tokens are valid for only a limited amount of time, so the authorization server frequently provides a pair of tokens. This parameter is required for single page apps using the authorization code flow. Be sure to check that the state value matches the one that you provided earlier in this procedure. NET Core, use Microsoft. See the following sections to learn how an API can validate and use the claims inside an access token. To call Microsoft Graph, the app makes an authorization request by attaching the access token as a Bearer token to the Authorization header in an HTTP request. The client application might explain to the user that its response is delayed to a temporary error. Set the version for applications by providing the appropriate value to the accessTokenAcceptedVersion setting in the app manifest. Note As a best practice, request the least privileged permissions that your app needs in order to access data and function correctly. In this article, you walked through the low-level protocol details usually required only when manually crafting and issuing raw HTTP requests to execute the authorization code flow. The following scopes represent the permission to access the user's profile:.
In computer systems, an access token contains the security credentials for a login session and identifies the user , the user's groups, the user's privileges, and, in some cases, a particular application.
Table of contents Exit focus mode. An access token is provided, which accesses the application or protected resource. Security tokens allow a client application to access protected resources on a resource server. Before the app can call the Microsoft identity platform endpoints or Microsoft Graph, it must be properly registered. Table of contents Exit focus mode. Clients should use the token response data that's returned with the access token for details on what's inside it. For the user, the actions that they can perform on the resource rely on the permissions that they have to access the resource. App-only access is used in scenarios such as automation and backup, and is mostly used by apps that run as background services or daemons. Access tokens enable clients to securely call protected web APIs. You're asked to complete the user flow's workflow.

0 thoughts on “Access token microsoft”