Vpn wikipedia
Mobile VPNs are used in environments where workers need to keep application sessions open at all times, throughout the working day, as they connect via various wireless networks, vpn wikipedia, encounter gaps in coverage, or suspend-and-resume their devices to preserve battery life. A conventional Vpn wikipedia cannot survive such events because the network tunnel is disrupted, causing applications to disconnect, time out, [1] fail, or even the computing device itself to crash. A VPN maintains an authenticated, encrypted tunnel for securely passing data traffic over public networks typically, the Internet.
Our secure VPN sends your internet traffic through an encrypted VPN tunnel to keep your browsing data safe, even over public or untrusted internet connections. As a Swiss VPN provider, we do not log user activity or share data with third parties. Our anonymous VPN service keeps your browsing history private and enables an internet without surveillance. Proton VPN breaks down the barriers of internet censorship, allowing you to access restricted online content. Our goal is to make online privacy accessible to all. We have focused on making the advanced security technology in Proton VPN easy to use and freely available. A secure internet connection you can trust is essential to maintaining your privacy on your laptop at home, your mobile device on the road, or your workstation at the office.
Vpn wikipedia
Therefore, when the connection is established, there will be no window pop up or similar, prompting one to start a certain program. Access to UHeM computers is available as long as the VPN connection is active, though one will need different programs to connect to the actual computers. The latter can be achieved through the use of an SSH Secure Shell connection text only interface where you can type and execute Linux commands or through a graphical interface. The older UHeM machines those accessed via lnode support NX , while the newer Sariyer cluster uses x2go for graphical interface connections. To transfer files, there are various available programs, such as scp , WinScp , Filezilla , etc. Manuals for these can be found on our Wiki site. The e-mail that you should have received with the confirmation of the creation of your account, also contains a link, together with the necessary username and password to access the VPN client software we provide for your convenience. The username and password mentioned, is only to download the VPN software. Once you download and install this software, you will need the following in order to establish the VPN connection:. The installation of the VPN client program varies with the operation system. The site that you used to download the software also contains installation instructions. Here we show the process for some of the most widely used operating systems. For earlier distributions, please check the web site address provided in the email. Write something in the Service Name part.
Tools Tools. Mullvad VPN.
View more global usage of this file. This file contains additional information, probably added from the digital camera or scanner used to create or digitize it. If the file has been modified from its original state, some details may not fully reflect the modified file. File:Virtual Private Network overview. Render this image in Marathi mr Ukrainian uk default language. This is a file from the Wikimedia Commons. Information from its description page there is shown below.
Last Updated: January 25, References. Luigi has over 25 years of experience in general computer repair, data recovery, virus removal, and upgrades. He is also the host of the Computer Man Show! This article has been viewed 1,, times. When you use a VPN, your internet activity is sent through an encrypted server that protects it from others on the network. This means your ISP, as well as other people using the same Wi-Fi network as you, can't see what you're doing online. If you're not using a VPN for work or school, you can select from a variety of paid and free VPN providers, most of which can be run on your computer, phone, or tablet. This wikiHow teaches you how to get started with a VPN. Research VPN services.
Vpn wikipedia
OpenVPN is a virtual private network VPN system that implements techniques to create secure point-to-point or site-to-site connections in routed or bridged configurations and remote access facilities. It implements both client and server applications. When used in a multiclient-server configuration, it allows the server to release an authentication certificate for every client, using signatures and certificate authority. It is capable of traversing network address translators NATs and firewalls.
Walmart saturn blvd san diego
Retrieved 2 August Another network is used to carry the data, which is encrypted. Some [a]. Enter your email address. Underlying virtual connection remains intact when the device switches to a different network; the mobile VPN handles the logins automatically. Yes; OpenVPN. Retrieved 28 July Understanding how much data people are using is a critical metric for TunnelBear. Retrieved October 16, In other projects.
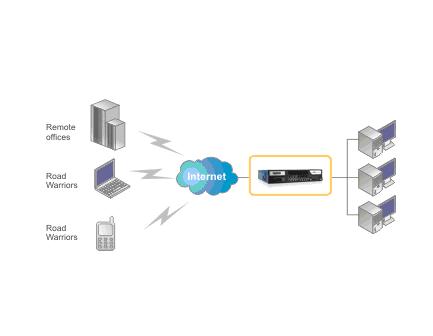
The laws of physics suggest wormholes through space and time are hypothetical; but wormholes do exist in cyberspace and wonders can be found on the other side. We call these cyberspace wormholes virtual private network VPN connections. In the diagram below the connection between the branch office and headquarters could be a permanent site to site VPN connection.
CiteSeerX In late , companies providing VPN services claimed the Great Firewall of China became able to "learn, discover and block" the encrypted communications methods used by a number of different VPN systems. Virtual Private Network. Netshield Ad-blocker. If the file has been modified from its original state, some details may not fully reflect the modified file. Tools Tools. When you launch Hotspot Shield. ISBN We support peerpeer P2P networking in some of our server locations. RSA [86]. If logging isn't mentioned in those sections but denied somewhere else on the website, the particular table cell will be marked as "No" in yellow and include an explanatory note. Why use a VPN. Read Edit View history. A VPN maintains an authenticated, encrypted tunnel for securely passing data traffic over public networks typically, the Internet. Data packets are secured by tamper proofing via a message authentication code MAC , which prevents the message from being altered or tampered without being rejected due to the MAC not matching with the altered data packet.

I agree with told all above. Let's discuss this question. Here or in PM.
It is very valuable phrase
So happens. We can communicate on this theme. Here or in PM.