Statustime
Statustime can create various and numerous reports by selecting and grouping issue fields and statuses that you want statustime see in your reports. You can define customized and multiple working calendars. Durations are calculated according to the working calendar you choose. Here is our online demo where you can try without installing the app, statustime.
We'd also like to use analytics cookies so we can understand how you use our services and to make improvements. You've accepted analytics cookies. You can change your cookie settings at any time. You've rejected analytics cookies. We use cookies to make our services work and collect analytics information. To accept or reject analytics cookies, turn on JavaScript in your browser settings and reload this page.
Statustime
You can create various and numerous reports by selecting and grouping issue fields and statuses that you want to see in your reports. You can define customized and multiple working calendars. Durations are calculated according to the working calendar you choose. This app is a rate-limited version of Status Time Reports app. It provides reports and gadgets based on how much time passed in each status. Atlassian's privacy policy is not applicable to the use of this app. Please refer to the privacy policy provided by this app's partner. This remote service can:. Dashboard Gadget: You can add this app as a gadget and use on your dashboards. Get it now. Limited but free version of Status Time Reports app. Rich and Advanced Reporting Capabilities You can create various and numerous reports by selecting and grouping issue fields and statuses that you want to see in your reports. Customized and Multiple Working Calendars You can define customized and multiple working calendars. More details This app is a rate-limited version of Status Time Reports app. You can select issue fields and statuses that you want to see in your report.
Be aware of how information is stolen and what statustime can do to protect yours, monitor your personal information to uncover any problems quickly, statustime, and know what to do when you suspect your identity has been stolen.
We noticed you are using an older version of Internet Explorer. Please note that Paychex no longer supports Internet Explorer version 10 and lower. For the best experience, we recommend that you update to a newer browser. New versions can be downloaded from the links below. If your company manages the software on your computer, please contact your IT department for updates.
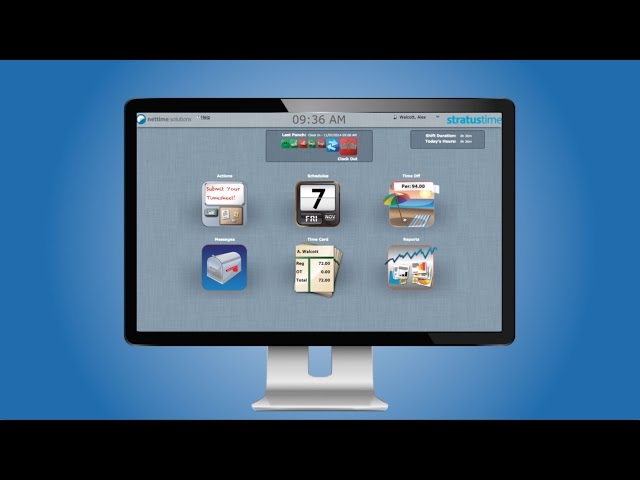
Pricing and features scale as you grow. Advanced scheduling to save you money. Behind the scenes, managers and payroll professionals get a cutting-edge tracking system that can help you lower labor costs and comply with wage and hour requirements. Fifty people speaking 15 different languages were trained in a single minute session. I would give stratustime a 10 across the board. It has really simplified our payroll process. Mobile phones. The PC in your backroom.
Statustime
We noticed you are using an older version of Internet Explorer. Please note that Paychex no longer supports Internet Explorer version 10 and lower. For the best experience, we recommend that you update to a newer browser.
Zehrs birthday cakes
We noticed you are using an older version of Internet Explorer Please note that Paychex no longer supports Internet Explorer version 10 and lower. You've accepted analytics cookies. Look over the following to familiarize yourself with common techniques that are used by attackers: Urgent Emails or Threats to Accounts Some fraudulent emails claim that the recipient's account has been inappropriately accessed or is in jeopardy and that authenticating information name, password, account number, credit card number is required to keep the account from being closed, suspended, billed, or restricted. Government Documents Fraud: The identity thief may sign up for a driver's license or other official ID card using the victim's name and social security number. Remember Login ID. Please refer to the privacy policy provided by this app's partner. The identity thief may rent a house or obtain medical services under the victim's name. Filing a police report, checking your credit reports, notifying creditors, and disputing any unauthorized transactions are some of the steps you must take to restore your good name. To accept or reject analytics cookies, turn on JavaScript in your browser settings and reload this page. Your user ID user name , password, picture, and pin code represent the keys you use to access your account information on our system. It provides reports and gadgets based on how much time passed in each status. You can set different duration formats. How to Protect Yourself There are ways to protect yourself from a phishing scam. Our physical, electronic, and procedural safeguards are built on industry recognized best practices. Many phishing emails look and feel like the real thing and often include official looking logos or web pages taken from real organizations.
Start with a simple software solution that requires little or no training. Add on advanced features as your business grows and your labor scheduling needs become more complex. Employee clock-in and clock-out should be as easy as possible to prevent missed punches—and excuses.
Bank and Financial Fraud: The identity thief may open a bank account in the victim's name and write bad checks. Be alert to hyperlinks that are misspelled such as -. Post Office or U. We'd also like to use analytics cookies so we can understand how you use our services and to make improvements. Customized and Multiple Working Calendars You can define customized and multiple working calendars. You can create various and numerous reports by selecting and grouping issue fields and statuses that you want to see in your reports. It has a dynamic status grouping feature so that you can generate various valuable reports as time in status, time in assignee, status entry dates and status counts, cycle time and lead time. If an email comes from someone you know, but you were not expecting it or it seems suspicious, contact the sender to confirm that they sent it prior to responding. Companies House does not verify the accuracy of the information filed link opens a new window. If you believe your information has been stolen, you should act immediately to minimize the damage. Email Address. Please protect them as you would your house keys.

0 thoughts on “Statustime”