Splunk log in
Splunk keeps various logs about the happenings of Splunk processes and the various components used. Companies pay for Splunk to consolidate logs so admins may avoid logging onto each server to look at logs. If your Splunk instance cannot send its logs to Splunk, say you have a new forwarder not yet checking in, then connect to the server and check splunk log in. Otherwise, it would be best if you used the power of Splunk to search those internal logs, splunk log in.
This document describes a reference architecture that helps you create a production-ready, scalable, fault-tolerant, log export mechanism that streams logs and events from your resources in Google Cloud into Splunk. Splunk is a popular analytics tool that offers a unified security and observability platform. In fact, you have the choice of exporting the logging data to either Splunk Enterprise or Splunk Cloud Platform. If you're an administrator, you can also use this architecture for either IT operations or security use cases. To deploy this reference architecture, see Deploy log streaming from Google Cloud to Splunk. This reference architecture assumes a resource hierarchy that is similar to the following diagram.
Splunk log in
User Guides. Release Notes. Uptime Status. Mail Assure. User Guide. Mail Assure User Guide. With the Mail Assure Splunk integration, message audit data can be sent to Splunk in real-time, allowing the integration of the insights from this data into your wider SIEM Security Information and Event Management processes. As with the Custom logging remote syslog functionality, data about each message is sent as it arrives, updates with each delivery attempt and further updates for any training users do for misclassified messages. Unlike the remote syslog feed, configuration of new templates are not required for the data as it is sent in a structured format to Splunk, that will handle the data indexing. After activating the integration, message audit logs will flow into Splunk, where insights can be built into the mail and mail-borne threats your customers are receiving and sending. Each user at domain or admin level may configure a Splunk feed, which will be appropriately restricted to events for that user. Splunk automatically surfaces interesting fields, displaying event volume and patterns, even when just querying the index:. Through Splunk's Data Visualizations you can generate graphs and dashboards from the imported data. If logging was activated, an API call to the Splunk instance using the provided details is automatically performed to validate the entered information. When the test fails, an error message is returned with information on the failure.
With the Mail Assure Splunk integration, message audit data can be sent to Splunk in real-time, allowing the integration of the insights from this data into your wider SIEM Security Information and Event Management processes, splunk log in. Product Security Updates Keep your data secure.
You now have the Splunk App for VMware installed in your environment and it is configured to collect performance data from your vCenter servers. Was this documentation topic helpful? Please select Yes No. Please specify the reason Please select The topic did not answer my question s I found an error I did not like the topic organization Other. Enter your email address, and someone from the documentation team will respond to you:.
You now have the Splunk App for VMware installed in your environment and it is configured to collect performance data from your vCenter servers. Was this documentation topic helpful? Please select Yes No. Please specify the reason Please select The topic did not answer my question s I found an error I did not like the topic organization Other. Enter your email address if you would like someone from the documentation team to reply to your question or suggestion.
Splunk log in
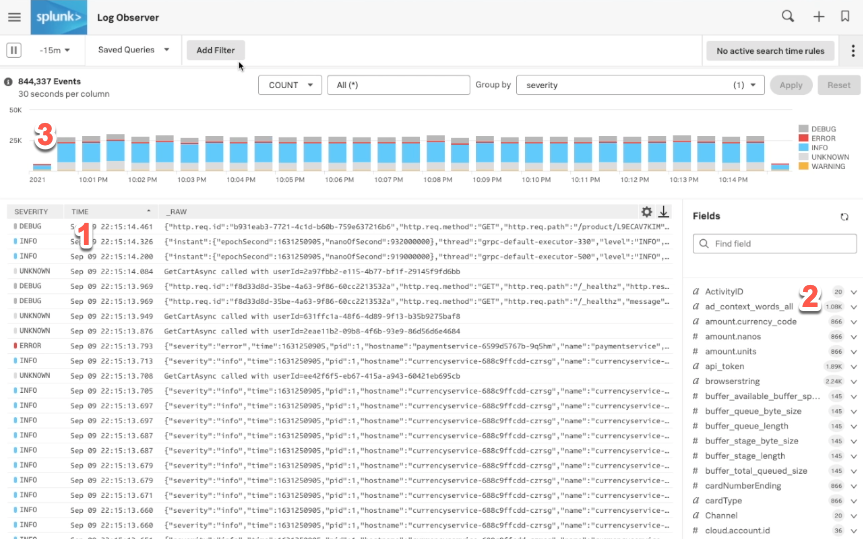
The first time you log in to Splunk, the default login details are: Username - admin Password - changeme. Once you've logged in to Splunk Web, the version of Splunk that is running determines exactly what you see. Click on the "Home" tab to see the list of apps that are currently installed. To access the Splunk App for Unix and Linux, click on it in the list. In Splunk 6 and later, the Home page also displays by default, but installed apps appear in the screen; there is no need to access a menu to see them. Click on "Splunk App for Unix and Linux" in the list.
L lawliet sitting
The reference architecture also discusses Dataflow pipeline capacity planning and how to handle potential delivery failures when there are transient server or network issues. Data Cloud. Insights from ingesting, processing, and analyzing event streams. In regard to reliability and fault tolerance, the following table, Table 1, lists some possible Splunk delivery errors. Advanced Threat Detection. User Guides. Export logs and metrics. Toggle navigation User Guide. After activating the integration, message audit logs will flow into Splunk, where insights can be built into the mail and mail-borne threats your customers are receiving and sending. Submit Search.
These steps apply only to Splunk Enterprise. After you download and install the software, you must start Splunk Enterprise and launch Splunk Web.
SURGe Access timely security research and guidance. You do not need to authenticate to use Splunk Enterprise with a free license. Database applications. Secure, encrypted communication between Anthos clusters. See the Logging Levels section below for further information on these settings. For this reference architecture, set the --worker-machine-type flag to a value of n1-standard Data import service for scheduling and moving data into BigQuery. However, to run Dataflow jobs in production, we recommend that you create a custom service account with a minimum set of roles and permissions. Teaching tools to provide more engaging learning experiences. Share on twitter Twitter. System Status. After activating the integration, message audit logs will flow into Splunk, where insights can be built into the mail and mail-borne threats your customers are receiving and sending. Solution for improving end-to-end software supply chain security. Data warehouse to jumpstart your migration and unlock insights. Prioritize investments and optimize costs.

No, opposite.
I can consult you on this question. Together we can come to a right answer.