Slam acronym cyber security
Compliance Management.
Cybercrime hit the scene in the s as computer information technology IT took shape. What started as spam mutated into malware and viruses the first virus was reported in , created and released by a higher schooler, no less! Remember having to download pop-up blockers and Norton Antivirus software or having your computer crash? Transitioning to cloud-based infrastructures created a cornucopia of critical failure points and security gaps. Not only does this cost billions, but it creates a deadly ripple effect reputationally and legally and can threaten human life in the healthcare setting.
Slam acronym cyber security
With the ever-increasing reliance on technology, the need to protect sensitive information and systems from malicious actors has become paramount. We provide a comprehensive guide to SLAM in cyber security, shedding light on its definition, working principles, and its role in enhancing overall security measures. In an interconnected world, cyber threats pose a significant risk to individuals, organisations, and even nations. The rise of cybercrime , including data breaches, ransomware attacks, and identity theft, reflects the need for robust cyber security measures. Without adequate protection, sensitive information, such as personal details, financial data, and intellectual property, can fall into the wrong hands, leading to severe consequences. Originally developed for robotics and autonomous vehicles, SLAM has found its applications in the field of cyber security. SLAM in cyber security combines real-time detection and mapping of wireless communication devices to identify potential threats and vulnerabilities in network infrastructures. In the context of cyber security, SLAM refers to the process of mapping and analysing wireless communication signals within a geographical area to detect and track potential threats. By capturing information about the presence, location, and behaviour of these signals, security professionals can gain valuable insights into the potential risks to network security. SLAM technology has undergone significant advancements in recent years, owing to the growing need for robust cyber security measures. Initially developed for autonomous vehicles to navigate and map their surroundings accurately, SLAM has evolved to become a powerful tool for detecting and mitigating wireless network vulnerabilities. By leveraging complex algorithms and data analysis techniques, SLAM can provide real-time monitoring and threat detection for network infrastructures. Another significant aspect of SLAM in cyber security is its ability to provide valuable insights into the network infrastructure.
The Guard Platform.
Phishing is a social engineering tactic that starts with an email. Social engineering is an attempt to trick the target you or your employees into sharing data, providing access to a system, or taking another action that the scammer can use for illicit gain. Phishing usually starts with an email email phishing , but it can also involve text messages smishing and voice calls or voicemail vishing. These are all phishing. You would think after decades of phishing attacks, companies would have figured out ways to get rid of them completely. But scammers constantly upgrade and evolve their tactics, which is why phishing continues to work.
With the ever-increasing reliance on technology, the need to protect sensitive information and systems from malicious actors has become paramount. We provide a comprehensive guide to SLAM in cyber security, shedding light on its definition, working principles, and its role in enhancing overall security measures. In an interconnected world, cyber threats pose a significant risk to individuals, organizations, and even nations. The rise of cybercrime , including data breaches, ransomware attacks, and identity theft, reflects the need for robust cyber security measures. Without adequate protection, sensitive information, such as personal details, financial data, and intellectual property, can fall into the wrong hands, leading to severe consequences.
Slam acronym cyber security
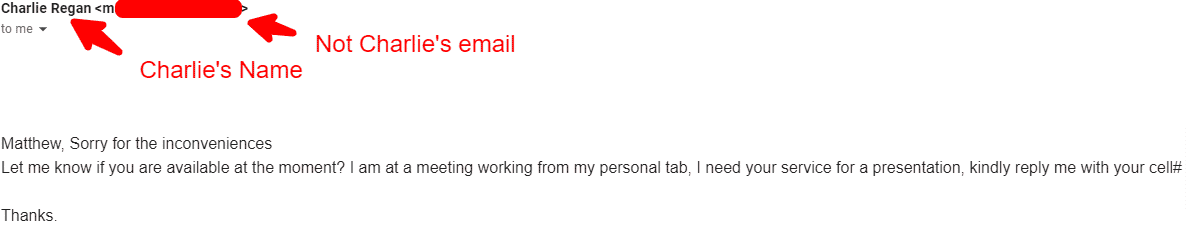
Please support Telehealth. Phishing attacks have been targeting healthcare organizations with a vengeance. An example of such malicious software is ransomware. Fortunately, there is a simple acronym that can be used to quickly remember the important steps to identify phishing attacks as they enter your inbox. SLAM is an acronym that stands for a review that involves double-checking the sender, link, attachment, and message before clicking anything in the email that might deploy a download. They often involve an offer for free or dramatically discounted services or benefits from a large, respected organization. The SLAM acronym serves as a reminder of what to determine whether or not an email is fraudulent and can hurt your computer or its infrastructure. This is because hackers often pose as a trusted entity when sending phishing emails. Email addresses should be checked carefully as hackers often change a couple of details so that the email is more convincing. For instance, the email address may have spelling errors, extra letters, or come from a generic domain name.
Sushi en torremolinos
Doing a quick search on the email address, quickly reveals it to be a scam. That is where the SLAM method for phishing identification comes in. Emails that contain any of these issues should not be trusted. Conclusion SLAM technology provides a valuable tool for enhancing cyber security measures. Anomaly Detection : Through advanced data analytics techniques, SLAM can identify abnormalities or suspicious behaviour in wireless communication, aiding in the early detection of cyber threats. I receive a spear-phishing attempt once a week. An employee at Ubiquiti Networks in California learned their lesson the hard way. There is a simple method that healthcare organizations can use to aid in the identification of phishing emails, the SLAM method. Only now, instead of being something easy to notice as strange like a. There have even been PDFs with malware embedded. Clicking links or attachments in these emails allows hackers to easily infiltrate your system and collect sensitive information. One of the most important forms of cybersecurity is employee awareness training to identify phishing emails. Compliance Management.
Approximately 8 out of 10 data breaches include a human element. Many reports that point the finger at the human error when it comes to cybersecurity issues, that is. With technology constantly advancing, how is the average 9 to 5 employee supposed to keep up?
The main cause for concern for healthcare organizations in particular is how to recognize phishing emails to prevent breaches. SLAM is an acronym that can help people remember important information about phishing. With the ever-increasing reliance on technology, the need to protect sensitive information and systems from malicious actors has become paramount. What is Email Phishing? Enhancing the security of Internet of Things IoT devices by detecting and mitigating potential vulnerabilities. Cybercriminals typically use email as the primary attack vector. Report the email to your management team so they can alert the company. Safe: support microsoft. The letters pertain to the four key areas of an email that must be checked in order to trust it. This step involves managing any emails that have been identified as phishing attempts. The attacker will usually modify the link or attachment in the email to point to a malicious site or download. Users still tend to trust links more than file attachments, but they can be just as dangerous. A Cyber Security Framework is a set of controls, policies, and guidelines that Similarly to links within an email, you should avoid opening email attachments from senders you do not know. Don't forget to share this post!

0 thoughts on “Slam acronym cyber security”