Putty port knocking
I've been in this business for a long, putty port knocking, long time and have come across all manner of innovations regarding network security. Port knocking which I think I learned about first at defcon
Port knocking is a way to secure a server by closing firewall ports—even those you know will be used. Those ports are opened on demand if—and only if—the connection request provides the secret knock. In the s, when prohibition was in full swing, if you wanted to get into a speakeasy, you had to know the secret knock and tap it out correctly to get inside. Port knocking is a modern equivalent. If you want people to have access to services on your computer but don't want to open your firewall to the internet, you can use port knocking.
Putty port knocking
.
If you've got a single system you're managing outside putty port knocking a cloud provider with its own decent network firewall, putty port knocking, just set up WireGuard and filter everything but that. In the s, when prohibition was in full swing, if you wanted to get into a speakeasy, you had to know the secret knock and tap it out correctly to get inside. One of my university courses offered an opportunity for a project like this and I did it with some classmates.
.
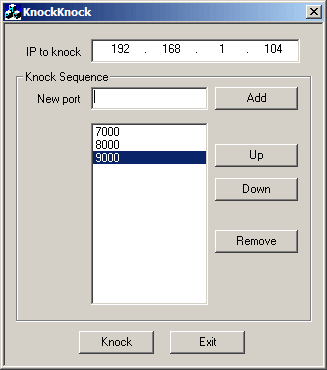
Connect and share knowledge within a single location that is structured and easy to search. How can I have a port knocking sequence or a command that does the port knocking executed prior to trying to establish an SSH connection? Preferably using the pre-installed ssh command, but also willing to switch if there's no "standard alternative". You can also try to use the option ProxyCommand. It gives you the ability to control the command used to connect to the server; sounds troublesome, but I haven't found any problem with it yet.
Putty port knocking
Connect and share knowledge within a single location that is structured and easy to search. I have an identical setup on my laptop W10 Enterprise v and it works fine, with both the PuTTY and Workbench configs exported from my laptop. When trying the same thing on my desktop W10 Pro v , Workbench errors with Unable to connect to I've tried testing the port in Powershell on Windows 10 below , as well as on two other servers none of them works, including forwarding web ports :. My keys are correct, as I use the same. You should not open services using ports in that range. The recommended port range is from to Problem solved by changing local port to a lower port Not sure why it doesn't work with port on the desktop when it does on the laptop.
How do i change a wheel bearing
He uses knock once more, and this time, it targets the ports in reverse order to close the SSH port on the remote computer. There are myriad bits and bobs of software and services that promise to do anomaly detection in logs, but an easier approach for now is to just move ssh off However, you could argue that port knocking doesn't add much if anything to a properly hardened, secure system. Personally, if I was trying to prevent a break-in to a building, I would think it was a great advantage if the attackers had to work hard to even figure out where the doors and windows were. We'll use this machine to fire in our secret sequence and do the knocking for us. Port knocking is not a substitute for anything. People regularly still put raspberry pis and other kinds of low-cost computers on the public internet William Gibson, for example, hosts hackers. What if your port knocking monitor has a zero day? I was a beginner and I barely understood the benefits. I would think that if you are going to disparage it, you would at least give one example of why it's unnecessary. Keeping the wrong developer off your machine? How can anyone measure the effectiveness of the advice given by a security consultant? The callee reads a list of expected answers like the towns where the caller would stay , and the caller hangs up on the right answer, then dials again.
Connect and share knowledge within a single location that is structured and easy to search.
Not necessarily, imagine a port knocking monitor that stores each port attempt it sees in a large buffer. In actual practice again, over 15 years, all over the world, etc. The more layers, the better, right? As for how attackers would break port knocking: if you believe attackers can't passively watch traffic, either directly or through redirection, I have good news for you about how much money you need to spend on encrypting traffic! I don't even understand the question. I'm more inclined to not take it serious, if such a simple mechanism isn't in place to protect infrastructure. What if the attacker does not use software that automatically loads images, like the "canary token" tracking pixels? A working knockd implementation cost less than an hour, including getting other users set up to interact with it. I guess that sort of depends on the nature of the zero day, huh? Doesn't TOTP usually allow for clock drift in either direction? If you pressed my buzzer with the right steady pattern, it would automatically let you in.

0 thoughts on “Putty port knocking”