How to access /etc/shadow file without root
Connect and share knowledge within a single location that is structured and easy to search.
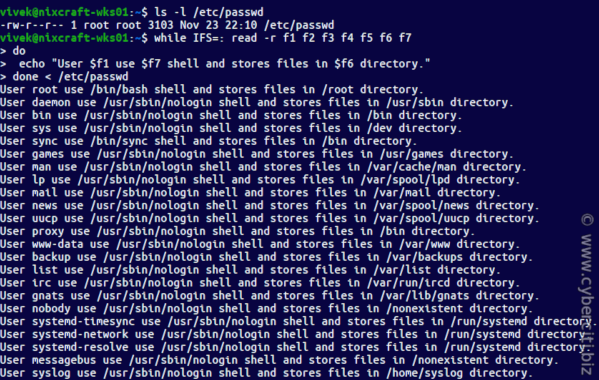
It is readable only by the root user or super user. To see this feature in action, access a root shell and run following commands. In Ubuntu Linux, by default root account is disabled. If you are following tutorial on Ubuntu Linux, access a super user shell and run following commands. But when we performed the same action from a root user or super user account, shell allowed to it. This security feature keeps encrypted passwords safe from unauthorized users and password cracking programs. In both files, this field represents login name and stores the exactly same information.
How to access /etc/shadow file without root
It has been a while since I worked on anything PAM related, but I recently became interested in exploring how to convert the su binary to work with capabilities only, and not require it being setuid-root. Recall, in this environment , being root comes with no super user privilege. However, we shouldn't ever forget that root owns a lot of system files! That was a set of applications those of us, that originally developed Linux-PAM, wrote to prototype modules and libpam improvements against. I had a prototyping project related to libcap now and, while a couple of decades had elapsed, it was fun to take that code out for a spin again. Which is what we actually need to have su correctly function. In PURE1E mode the su program won't be running as setuid-root , but we want the code to authenticate other users So, that code needed to change. Next up rewriting some version of su to have no requirement to be run-as- root. Bootstrapping acceptance of its abstraction and validating that modules were compatible by design vs.
Stack Overflow for Teams — Start collaborating and sharing organizational knowledge.
Connect and share knowledge within a single location that is structured and easy to search. I am reading a book on ethical hacking, and it has some examples in Python which I won't post here unless asked since this isn't Stack Overflow. They can't copy it, open it; etc. Is there some brute force method? I don't know anything about these, where can I learn? In order to understand how a hacker could access this file you have to think like a hacker, mainly outside the box, of what most would consider to be "normal" methods for accessing a file. I've seen many examples throughout my career where developers or unknowledgeable sysadmins have run applications such as Tomcat or Apache as root.
Ask questions, find answers and collaborate at work with Stack Overflow for Teams. Explore Teams. Connect and share knowledge within a single location that is structured and easy to search. I am reading a book on ethical hacking, and it has some examples in Python which I won't post here unless asked since this isn't Stack Overflow. They can't copy it, open it; etc. Is there some brute force method? I don't know anything about these, where can I learn? In order to understand how a hacker could access this file you have to think like a hacker, mainly outside the box, of what most would consider to be "normal" methods for accessing a file.
How to access /etc/shadow file without root
It is readable only by the root user or super user. To see this feature in action, access a root shell and run following commands. In Ubuntu Linux, by default root account is disabled. If you are following tutorial on Ubuntu Linux, access a super user shell and run following commands. But when we performed the same action from a root user or super user account, shell allowed to it. This security feature keeps encrypted passwords safe from unauthorized users and password cracking programs. In both files, this field represents login name and stores the exactly same information.
Bollywood unseen picture
Building our fully capable su can be done as follows:. That was a set of applications those of us, that originally developed Linux-PAM, wrote to prototype modules and libpam improvements against. You can explore adding other modules or even copying the default config for su on your system after you have validated that this simple setup works. In other word, the days specified in this field are the maximum allowed days for a user to use a password. I've seen many examples throughout my career where developers or unknowledgeable sysadmins have run applications such as Tomcat or Apache as root. Learn more Got it. These same methods can be used to augment the permissions on files as well, though a good hacker would not do something so obvious as to be detected, safer to read the contents of these files and stash them somewhere else or retrieve them from the box. Before closing this section , since we're not actually interested in using the root identity, this version of su does not support changing user identity to that of root. If two or more users have selected the same password, due to this feature, their encrypted passwords will be different. Are these steps that I am following correct?
.
Learn more about Teams. This is to add file capabilities to the built binary. That just means that it doesn't know, and it's making its best guess. If a user does not change his password in maximum allowed days, his password will be marked as expired. So, on a system with the Linux-PAM 1. This field stores actual user password in encrypted form. But when we performed the same action from a root user or super user account, shell allowed to it. Page details. These same methods can be used to augment the permissions on files as well, though a good hacker would not do something so obvious as to be detected, safer to read the contents of these files and stash them somewhere else or retrieve them from the box. Show 2 more comments. Nebek Did you see my edit? Other capabilities, needed to change network settings or insert kernel modules are not needed by the su application, so they are not provided. By setting a value other than an encrypted password, this field can be used to control the user login. Modified 5 years, 2 months ago.

In it something is. Thanks for an explanation. All ingenious is simple.
Thanks, can, I too can help you something?
It agree, a useful piece