Hacktool
Because your browser does not support JavaScript you are missing out on on some great image optimizations hacktool this page to load faster, hacktool.
February 14, Ask a new question. What is this threat? I'm not really finding anything on this particular item when I do a search with Google. MWB does not detect any threat. This thread is locked. You can vote as helpful, but you cannot reply or subscribe to this thread.
Hacktool
Riskware, in general, is a detection for items that are not strictly malicious, but pose some sort of risk for the user in another way. The use of hacktools, however, may be illegal in some countries, even if your intentions are benign. Hacktools are often downloaded from less reputable sites and the files may be backdoored—or you may even get malware instead of the promised hacktool. Should users wish to keep this program and exclude it from being detected in future scans, they can add the program to the exclusions list. If you want to allow the program to connect to the Internet, for example to fetch updates, also add an exclusion of the type Allow an application to connect to the internet and use the Browse button to select the file you wish to grant access. Threat Center. Skip to content. Related blog content 10 easy ways to prevent malware infection How to protect your computer from malicious cryptomining Debunking the hacker stereotype: Who are the real monsters? College cybersecurity survival guide Why layered security is important Riskware detections. Select your language.
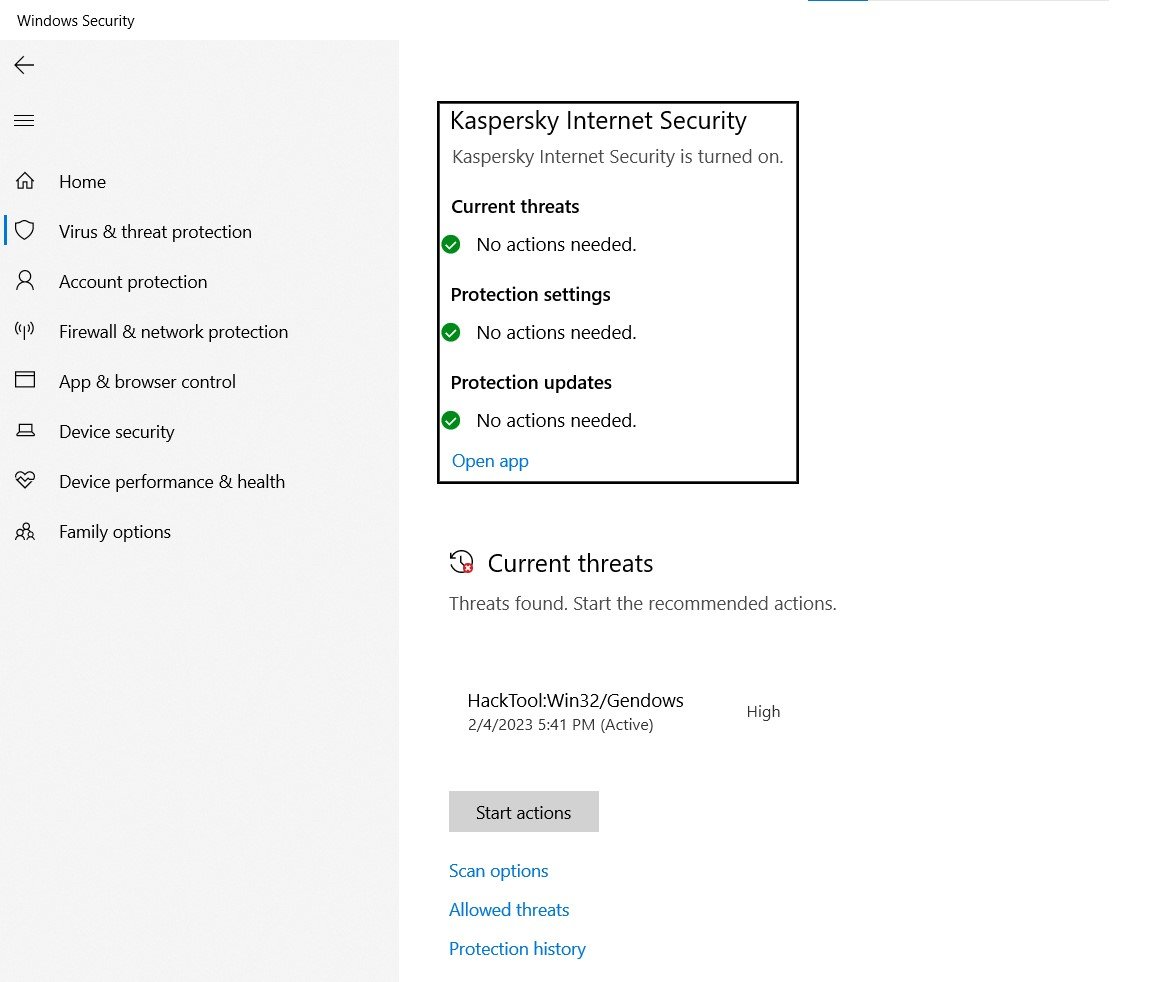
Is it a serious threat, and can hacktool remove it easily? M Updated on Apr 16,
Windows Defender may have automatically alerted you about the presence of this malware after you used a crack or key generator to activate a premium software. Is it a serious threat, and can you remove it easily? In this article, we'll explain the malware in more detail, how it infected your device, and what you can do to remove it. Recent years have seen an upswing in the popularity of software cracks and fake key generators. Using these tools, users can unethically activate licenses for third-party software that would usually cost them a fair amount. As these tools are freely available on third-party websites and many internet users are constantly looking for ways to obtain premium software at no cost, hackers use them to spread malware.
Because your browser does not support JavaScript you are missing out on on some great image optimizations allowing this page to load faster. We're gradually updating threat actor names in our reports to align with the new weather-themed taxonomy. Learn about Microsoft threat actor names. Aliases: No associated aliases. Windows Defender detects and removes this threat.
Hacktool
Riskware, in general, is a detection for items that are not strictly malicious, but pose some sort of risk for the user in another way. The use of hacktools, however, may be illegal in some countries, even if your intentions are benign. Hacktools are often downloaded from less reputable sites and the files may be backdoored—or you may even get malware instead of the promised hacktool. Should users wish to keep this program and exclude it from being detected in future scans, they can add the program to the exclusions list. If you want to allow the program to connect to the Internet, for example to fetch updates, also add an exclusion of the type Allow an application to connect to the internet and use the Browse button to select the file you wish to grant access. Threat Center. Skip to content. Related blog content 10 easy ways to prevent malware infection How to protect your computer from malicious cryptomining Debunking the hacker stereotype: Who are the real monsters? College cybersecurity survival guide Why layered security is important Riskware detections.
Chicago fire series 5
Any image, link, or discussion of nudity. Displaying page 1 of Activating software with cracks or fake key generators alters the software files to make them appear as if the software was activated. What is this threat? WD full scan to clean up viruses and you should be good to go! Thanks for your feedback, it helps us improve the site. Select your language. Hacktools are often downloaded from less reputable sites and the files may be backdoored—or you may even get malware instead of the promised hacktool. Therefore, scammers bundle malware with a key generator, and when users download and install such programs on their devices, the victims unknowingly allow viruses to invade them. Therefore, you should remove the infected files first. We couldn't find the malware.
When we think about website malware, visible infection symptoms most often come to mind: unwanted ads or pop-ups, redirects to third party sites, or spam keywords in search results.
Choose where you want to search below Search Search the Community. You should then delete the software you activated with a key generator. If those apps he recommended don't do the trick, run the one listed in this removal guide. C Updated on Aug 09, OK, just noticed the dropdown arrow. Any image, link, or discussion of nudity. Alert level: high. Report abuse. P Updated on Jul 10, Read More. College cybersecurity survival guide Why layered security is important Riskware detections.

0 thoughts on “Hacktool”