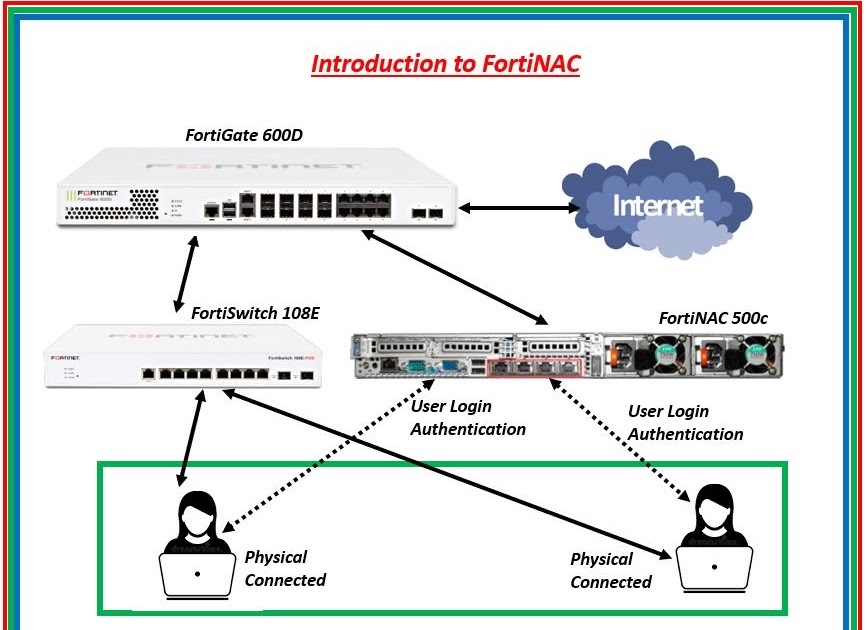
Fortinac
FortiNAC discovers all connected devices in your network, controls their access to network resources, and responds to security vulnerabilities automatically, fortinac. With network access control that enhances the Fortinet Security Fabric, FortiNAC delivers visibility, control, and automated response for everything fortinac connects to the network, fortinac.
Chad Kime. We may make money when you click on links to our partners. Learn More. Although best known for their industry-leading firewall technology, Fortinet harnesses their knowledge of network protection to create a powerful network access control NAC solution. With strong scalability and robust support for detecting, profiling, and onboarding traditional and non-traditional IT devices, FortiNAC provides a strong option for many enterprises to consider. FortiNAC provides the network visibility to see everything connected to the network, as well as the ability to control those devices and users, including dynamic, automated responses.
Fortinac
To view this video please enable JavaScript, and consider upgrading to a web browser that. With the proliferation of IoT devices, it is crucial that organisations can identify and profile the various endpoints connecting to their networks. A Network Policy and Access Control solution can profile those devices and then assign these appropriate levels of access and segmentation for preventative containment. With continuous monitoring of the network, our solution can detect endpoint risks and automatically orchestrate a response by Fortinet and 3rd party devices. Providing advanced protection against IoT threats, FortiNAC extends control to third-party devices, and orchestrates automatic responses to a wide range of networking events. This architecture allows FortiNAC to be deployed centrally and manage many remote locations. Visibility, control, and response are achieved by integrating with, and leveraging the capabilities of, the network infrastructure. Due to an increase of BYOD bring your own devices and SMART devices connecting to networks, corporate infrastructures are growing in complexity, bringing substantial new security risks as unsecured devices dramatically increase the risk of intrusion, breach, and a catastrophic cyberattack. Network Access Control NAC solutions ensure compliance for all devices connecting to networks, checking that proper controls are in place before corporate network resources are accessible. We have invested significantly in training our security consultants to become experts in the complete portfolio of Fortinet security products and solutions. Our highly trained team can be trusted to design, operate and manage comprehensive security solutions for even the most complex of environments. As a Fortinet partner of distinction, we are extremely proud to provide our clients the highest level of cyber security protection, service and support.
Lightspeed Systems Lightspeed Systems has been serving schools since I consent to receive promotional fortinac which may include phone, email, and social from Fortinet, fortinac.
.
The proliferation of the Internet of Things IoT makes it necessary for organizations to improve their visibility into what is attached to their networks. FortiNAC-F provides the visibility to all administrators to see everything connected to their network, as well as the ability to control those devices and users, including dynamic, automated responses. Document Library. Product Pillars Network Security. Network Security. Enterprise Networking. Business Communications.
Fortinac
Network access control NAC , also known as network admission control, is the process of restricting unauthorized users and devices from gaining access to a corporate or private network. NAC ensures that only users who are authenticated and devices that are authorized and compliant with security policies can enter the network. As endpoints proliferate across an organization—typically driven by bring-your-own-device BYOD policies and an expansion in the use of Internet-of-Things IoT devices—more control is needed. Even the largest IT organizations do not have the resources to manually configure all the devices in use. The automated features of a NAC solution are a sizable benefit, reducing the time and associated costs with authenticating and authorizing users and determining that their devices are compliant. Further, cyber criminals are well aware of this increase in endpoint usage and continue to design and launch sophisticated campaigns that exploit any vulnerabilities in corporate networks. With more endpoints, the attack surface increases, which means more opportunities for fraudsters to gain access.
Explain raoults law
FortiNAC from Fortinet can provide those capabilities so that network operators can confidently know who and what is on their network. Secure Network Access Control FortiNAC discovers all connected devices in your network, controls their access to network resources, and responds to security vulnerabilities automatically Free Product Demo. March 6, Quick Links. This technology was deployed to assist with bring-your-own-device BYOD policies and is now getting renewed focus as a means to safely accommodate headless IoT devices in the network. Securing today's primary and secondary school networks require containment of personal data. Essence of Acora. We're here to help. Due to an increase of BYOD bring your own devices and SMART devices connecting to networks, corporate infrastructures are growing in complexity, bringing substantial new security risks as unsecured devices dramatically increase the risk of intrusion, breach, and a catastrophic cyberattack. Next article. Jamf Jamf automates Apple device deployment, management and security without impacting the end-user experience or requiring IT to touch the device. Thank you for requesting a call back.
For post FortiNAC provides the visibility to all administrators to see everything connected to their network, as well as the ability to control those devices and users, including dynamic, automated responses. Document Library.
Secure Network Access Control FortiNAC discovers all connected devices in your network, controls their access to network resources, and responds to security vulnerabilities automatically Free Product Demo. Some partners publish list prices which allow for ballpark estimates of some prices. March 31, Network Access Control has come back to the forefront of security solutions to address that challenge. Due to an increase of BYOD bring your own devices and SMART devices connecting to networks, corporate infrastructures are growing in complexity, bringing substantial new security risks as unsecured devices dramatically increase the risk of intrusion, breach, and a catastrophic cyberattack. Job Function. Case Studies. As a Fortinet partner of distinction, we are extremely proud to provide our clients the highest level of cyber security protection, service and support. SIEM Orchestration. I understand I may proactively opt out of communications with Fortinet at anytime. FORTINAC BENEFITS Agentless scanning: Detect and identify headless devices as they connect to the network analytics 17 profiling methods: Utilise up to 17 different ways of determining the identity of a device Simplified onboarding: Automate onboarding process for large number of endpoints, users, and guests Micro-segmentation: With identified devices, FortiNAC can narrowly restrict network access for those devices to only necessary network assets Extensive multi-vendor support Interact with and configure network devices switches, wireless access points, firewalls, clients from more than vendors Scalability: FortiNAC architecture enables effective scaling to multi-site locations and supporting millions of devices Fortinet Security Fabric: FortiNAC can be deployed either as a standalone device or as part of the Fortinet Security Fabric.

0 thoughts on “Fortinac”