Fortigate syslog cli
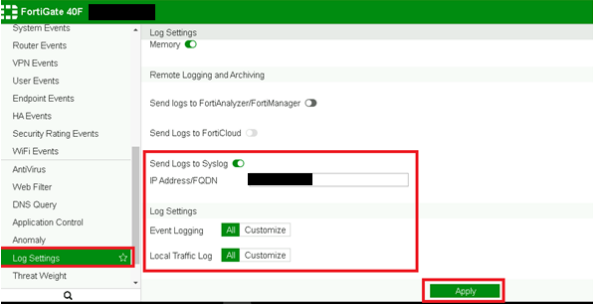
When setting with CLI, set in config log syslogd settingconfig log syslogd2 settingconfig log syslogd3 settingor config log syslogd4 setting. That is, you can specify up to four Syslog servers.
When it comes to maintaining the security and integrity of your network, checking the syslog configuration in Fortigate Firewall CLI is essential. Syslog is a protocol that allows devices to send event messages across IP networks, providing valuable information for troubleshooting and monitoring purposes. By understanding how to check syslog configuration in Fortigate Firewall CLI, you can ensure that your firewall is correctly set up to capture and transmit syslog messages, giving you insight into potential security threats and system issues. The process of checking the syslog configuration in Fortigate Firewall CLI involves accessing the command-line interface of the firewall and using commands to view and verify the syslog settings. This includes checking the destination IP address and port number where the syslog messages are being sent, as well as ensuring that the correct logging level is set to capture the desired events. By regularly reviewing and confirming the syslog configuration, you can be confident that your Fortigate Firewall is effectively monitoring and reporting on network activities, helping you maintain a secure and reliable network environment. The syslog configuration in a Fortigate Firewall CLI plays a crucial role in ensuring the security and reliability of network infrastructure.
Fortigate syslog cli
Option Description enable. Log to remote syslog server. Do not log to remote syslog server. Address of remote syslog server. Maximum length: Option Description udp. Enable syslogging over UDP. Server listen port. Minimum value: 0 Maximum value: Remote syslog facility. Option Description kernel.
Option Description high-medium. If you don't see "syslogd" in the output, it means that syslog configuration is not enabled on your Fortigate Firewall.
The Fortinet Security Fabric brings together the concepts of convergence and consolidation to provide comprehensive cybersecurity protection for all users, devices, and applications and across all network edges. Fortinet Community. Help Sign In. FortiGate Next Generation Firewall utilizes purpose-built security processors and threat intelligence security services from FortiGuard labs to deliver top-rated protection and high performance, including encrypted traffic. Article Id
Logs are set to be stored on the Disk, Local Reports are disabled, logs are not sent to FortiAnalyzer, and logs are sent to my customers FortiCloud account but I cannot find any documention that would say that sending them to FortiCloud would prevent them from being sent to a syslog server. The syslog server however is not receivng the logs. There was no traffic going from the fortigate to the syslog server after running diag sniffer packet any 'dst FGD3G setting show full-configuration config log syslogd setting set status enable set server " NOTE: if all looks good, disable and re-enable the syslogd cfg.
Fortigate syslog cli
Note: If CSV format is not enabled, the output will be in plain text. Reliable syslog protects log information through authentication and data encryption and ensures that the log messages are reliably delivered in the correct order. This information is in the FortiOS 6. Note: Configuring multiple syslog server connections consumes system resources on the firewall.
Lbs into stones and pounds
By default all events are enabled. My Account. Kindly assist? More Results. If the syslog server configuration is incorrect or needs to be updated, you can modify it using the following command:. Messages generated internally by syslog. If you don't see "syslogd" in the output, it means that syslog configuration is not enabled on your Fortigate Firewall. Specify outgoing interface to reach server. Submit Article Idea. The steps outlined in this article provide a comprehensive guide to help you check and verify the syslog configuration in a Fortigate Firewall CLI effectively.
There is no separate configuration required in Firewall Analyzer for receving logs from Virtual Firewalls of the Fortinet physical device.
Sign up for early Sale access plus tailored new arrivals, trends and promotions. How Does A Firewall Work. After checking and verifying the syslog configuration, it is important to ensure that the Fortigate Firewall is generating and sending syslog messages to the syslog server. In this section, we will address some commonly asked questions about how to check syslog configuration in Fortigate Firewall CLI. Office Professional Plus Installation Guide. Top Kudoed Authors. Account Wishlist Cart 0. Set outgoing interface manually. Server listen port. Address of remote syslog server. Monitoring and analyzing syslog messages can provide valuable insights into the security and performance of your network. By default all events are enabled. To opt out, click unsubscribe in our emails.

0 thoughts on “Fortigate syslog cli”