Cisco internet edge design
The Secure Edge is a place in the network PIN where a company connects to the public Internet, service providers, partners, and customers.
Updated: Nov 2, Ready to live on the edge? In the last design post we talked about remote access VPN, but in this 4th installment of the network design scenario series we will take a detailed look at designs for the network edge. What is the network edge? The network edge is where your network and outside networks connect. In the enterprise world this is your path out to the internet, in the provider world this is generally where you connect to upstream providers or peers. We will cover high and low level designs, different types of topologies such as SMB, enterprise and service provider SP , look at the building blocks, redundancy options and other considerations.
Cisco internet edge design
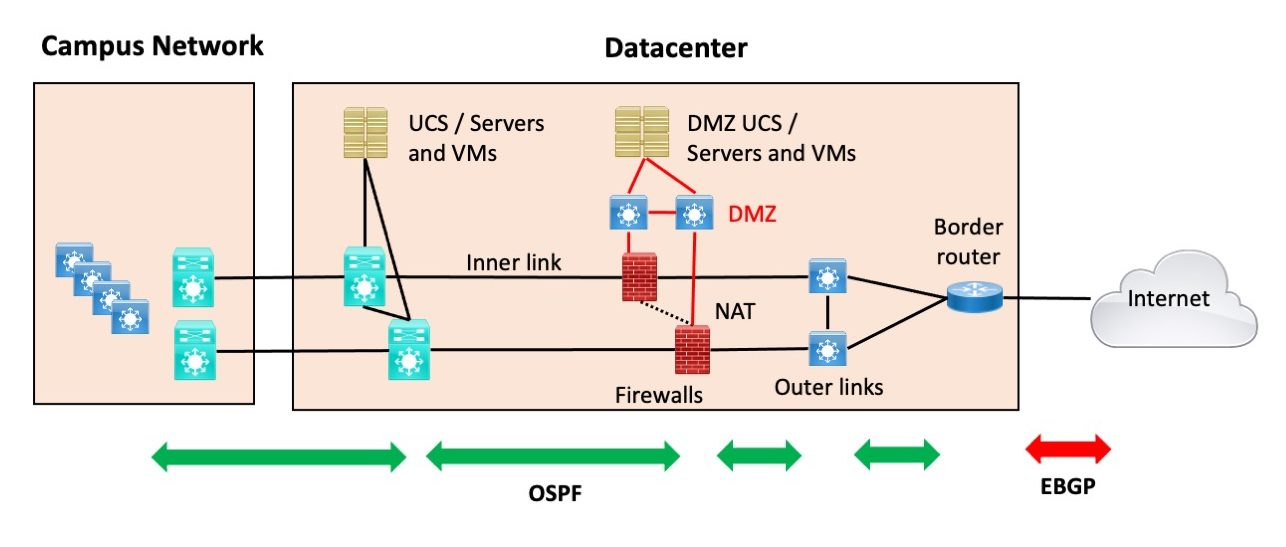
By Internet Edge, I specifically mean connecting your data center s to the Internet. For those who liked the SD-Access blog series: I have a few more SD-Access blogs fermenting in my brain and hope to be posting them after this series. Teaser: SD-Access Transit with two data centers and two pairs of fusion firewalls. There are some things to be aware of and design for. Ahem, so Internet Edge. More specifically, how you design the Internet connectivity in a data center or two. Lots of double devices. We may get into that topic later in the series. Also not shown, since it more of a non-Internet Edge security design issue: most sites now have a firewall between users onsite and remote access and the servers. In my SD-Access designs, it might be the fusion firewall.
Stay tuned!
For cloud-enabled enterprises, the availability of their Internet facing-infrastructure is of critical importance. Cisco found that an average enterprise uses cloud services. Even relatively short Internet outages will adversely impact mission-critical cloud workloads. This results in significant costs and damage to reputations. Many enterprises may be unaware of just how significant their internet services have become to their overall business viability. The aim of this post is to outline four 4 alternate internet designs that address the shortcomings of a single unreliable internet link.
For cloud-enabled enterprises, the availability of their Internet facing-infrastructure is of critical importance. Cisco found that an average enterprise uses cloud services. Even relatively short Internet outages will adversely impact mission-critical cloud workloads. This results in significant costs and damage to reputations. Many enterprises may be unaware of just how significant their internet services have become to their overall business viability. The aim of this post is to outline four 4 alternate internet designs that address the shortcomings of a single unreliable internet link. Only internet-facing routers are in scope for this discussion. They are the routers shaded in red shown in Figure 1. Option 1 is known as a single-homed design.
Cisco internet edge design
Use our validated guides to design your SD-WAN and deliver a great user experience for branches and remote sites. Skip to content Skip to search Skip to footer. Contact Cisco Get a call from Sales. Featured guides. WAN security Set up pervasive security policies to protect your network, data, and users. Internet edge The gateway to the Internet needs to be more agile and secure in the digital age. Application policy management Use EasyQoS for simplified and consistent application policy management. The guide focuses on the step-by-step procedures for defining the network characteristics requirements for an application and leveraging the calculated path liveness and quality measurement to influence the traffic path dynamically, providing the best experience for the applications at all times. A high-level discussion of components, on-boarding of WAN devices, controller connections, configuration templates, and policies is covered, in addition to deployment planning considerations. However, the document is not meant to exhaustively cover all options.
Dota sniper build
In this guide, you will learn about the different certificate options available on the Cisco SD-WAN controller complex and how to deploy them, along with the whitelist authorization file. It is also the most complex and expensive to design and implement. Threat Intelligence: Contextual knowledge of existing and emerging hazards. This simplifies inspection capabilities and ensures that no traffic loss occurs in the event of a failover. When in data centers it will be important to ensure your cross connects utilize different equipment as even with different internet providers that could be a single point of failure. Tracking against URL-based threats. Notice in the diagram we are using the BGP attribute local preference to mark inbound routes which gives the outbound traffic a way to decide which outgoing path to go on. The Secure Edge architecture is logically arranged into five layers to provide a company with several lines of defense from the threats that exist in public networks. WAN security Set up pervasive security policies to protect your network, data, and users. There are limited methods for improving this design, but a redundant power supply could be installed in the internet router. As mentioned before it would probably be better to use your public v4 IP space in the DMZ for routing purposes, and if using public NAT pools on the firewalls it will be easier for reachability, as you could just advertise those subnets via iBGP to the edge routers; with OSPF you'd likely have to redistribute a static of the NAT pools. Worm traffic that exhibits scanning behavior. Enterprise High Level Design.
.
Functional Control Definition Secure Applications Applications require sufficient security controls for protection. This network would probably have 2 blocks of provider assigned IP blocks and just performing NAT out each connection based on where traffic is exiting, that would facilitate the outside routing back to the network. Then for outbound traffic you will utilize local preference from the provider received routes in order to ensure your traffic leaves out the right connection. Web access is a requirement for the day-to-day functions of most organizations. Attacks using worms, viruses, or other techniques. Weight often comes up but that is only for the configured router and not recommended. What is the network edge? To close out - we covered many aspects of the network edge from connecting to your service provider or other providers , having adequate diversity, to the challenges of routing in and out of the network. Identity-based access. Email Security: Messaging integrity and protections. Communities: Chinese Japanese Korean.

I consider, that you are not right. I am assured. Write to me in PM, we will communicate.
Bravo, your opinion is useful
In my opinion you are not right. I can defend the position. Write to me in PM.