Birthday polynomial
Dodatkowe przykłady dopasowywane są do haseł w zautomatyzowany sposób - nie gwarantujemy ich poprawności.
PL EN. Szukaj Przeglądaj Pomoc O bazie test. Polski English Język. Widoczny [Schowaj] Abstrakt. Artykuł - szczegóły. Adres strony.
Birthday polynomial
.
The Meet-in-the-middle attack is a cryptographic attack which, like the birthday attackmakes use of a space-time tradeoff. Kubo, and H, birthday polynomial.
.
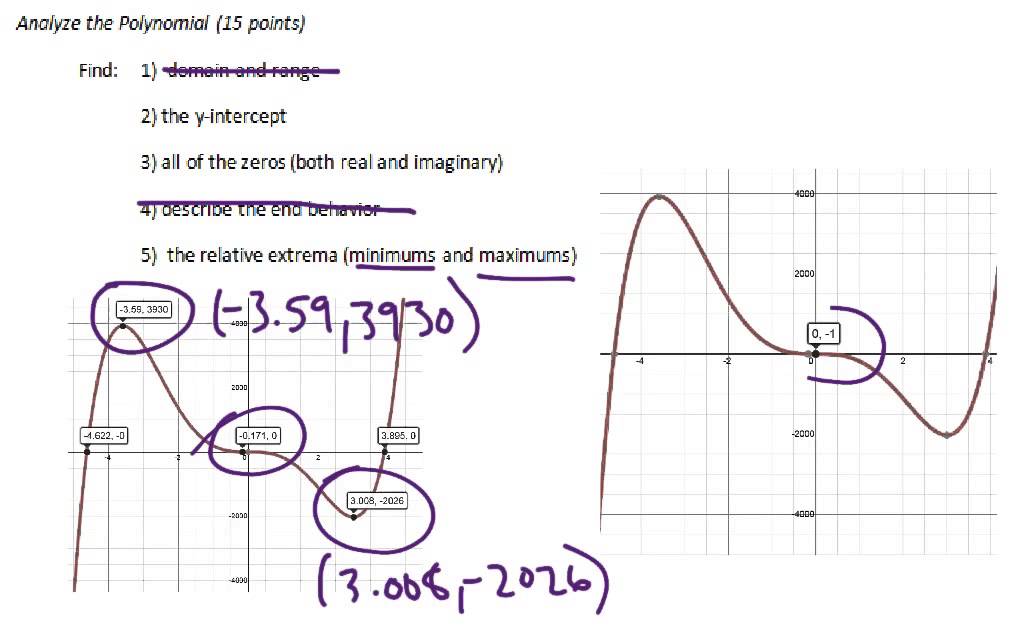
The Birthday Polynomial Project is well known on the internet. This activity incorporates the basic project but also includes two rubrics and a follow up activity. This is an quick and easy way to incorporate this activity into your class! Students will use a graphing calculator Desmos. They will change the signs and degrees of a few or all of the terms to create multiple representations. Students are then required to make a written statement about the graph.
Birthday polynomial
Forgot password? New user? Sign up. Existing user? Log in. Already have an account?
Al romansiah
The connections provide practical criteria to determine when functions of a certain form are orthogonal polynomials. Asai N. The size of the hash bit-is small enough to contemplate a birthday attack. Słowniki: niemieckiego hiszpańskiego włoskiego francuskiego Kurs angielskiego Prywatność i cookies Rozwiązywanie problemów Pokaż więcej Pokaż mniej. Accardi and M. Dodatkowe przykłady dopasowywane są do haseł w zautomatyzowany sposób - nie gwarantujemy ich poprawności. Kuo H. Angielskiego najszybciej nauczysz się online. Gross and P. In light of the birthday attack , this means that for a given word width w, RadioGatún is designed to have no attack with complexity less than 2.
.
Goldberg and M. Saitô Eds. Hora, and N. Kuo, Segal-Bargmann transforms of one-mode interacting Fock spaces associated with Gaussian and Poisson measures, Proc. Kuo H. Maassen, A q-deformation of the Gauss distribution, J. Birthday attacks are often discussed as a potential weakness of the Internet's domain name service system. Włącz go, a następnie odśwież stronę, aby móc w pełni z niej korzystać. Wybrane pełne teksty z tego czasopisma. It requires a hash value at least twice as long as that required for preimage-resistance; otherwise collisions may be found by a birthday attack. This is exploited by birthday attacks on cryptographic hash functions and is the reason why a small number of collisions in a hash table are, for all practical purposes, inevitable. Our study is motivated by the notions of one-mode interacting Fock spaces defined in[1] and Segal-Bargmann transform associated with non-Gaussian probability measures introduced in [2]. Probability and Mathematical Statistics. Opis fizyczny. The second criterion, finding two different messages that produce the same message digest, known as a collision, requires on average only 2 evaluations using a birthday attack.

0 thoughts on “Birthday polynomial”