Avg ransomware decryption tool
Keep reading to learn how ransomware works, different types, avg ransomware decryption tool noteworthy examples of recent attacks. Get it for MacPCAndroid. Get it for AndroidiOSMac. Ransomware is malicious software that encrypts files on your computer or locks your device and demands a ransom in exchange for decryption.
The healthcare sector and financial industry are especially vulnerable to ransomware attacks , as they store valuable personally identifiable data PII which can be misused to carry out lucrative crimes, like identity theft and fraud. During a successful ransomware attack, cyber attackers encrypt this sensitive data , preventing organizations from accessing it. The attackers then demand a hefty cryptocurrency ransom payment in exchange for a decryption key that provides access to it again. If your organization is infected by ransomware, time is of the essence to prevent further data breaches. Thankfully, there are now many free decryption tools available to help you defend against common variants of ransomware. Read on to learn how to decrypt ransomware and prevent future infections through defensive measures. Skip ahead to our list of the top 10 free ransomware decryption tools.
Avg ransomware decryption tool
All Resources. Visit Blog. Read Report. Read Case Study. Join the Team. Ransomware is one of the most vicious cyber threats out there right now. A dangerous form of malware , it encrypts files and holds them hostage in exchange for payment. Luckily for you, there are plenty of ransomware decryption tools that you can use to get access to your files without needing to pay the ransom. If your network gets infected with ransomware , follow the mitigation steps below and use this list with over ransomware decryption tools. Step 1: Do not pay the ransom because there is no guarantee that the ransomware creators will give you access to your data.
Alma ransomware decryption tool Alma Locker is a dangerous malware that encrypts files with AES encryption. The project aims to help victims of ransomware retrieve their encrypted data and avoid paying ransom to cybercriminals.
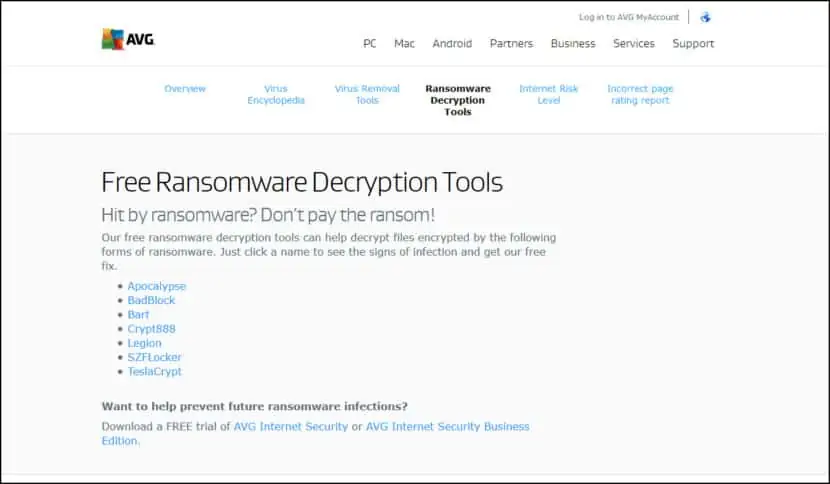
Our free ransomware decryption tools can help decrypt files encrypted by the following forms of ransomware. Just click a name to see the signs of infection and get our free fix. Learn more about our business security solutions. Apocalypse adds. FuckYourData ,. Encryptedfile , or.
The healthcare sector and financial industry are especially vulnerable to ransomware attacks , as they store valuable personally identifiable data PII which can be misused to carry out lucrative crimes, like identity theft and fraud. During a successful ransomware attack, cyber attackers encrypt this sensitive data , preventing organizations from accessing it. The attackers then demand a hefty cryptocurrency ransom payment in exchange for a decryption key that provides access to it again. If your organization is infected by ransomware, time is of the essence to prevent further data breaches. Thankfully, there are now many free decryption tools available to help you defend against common variants of ransomware.
Avg ransomware decryption tool
Ransomware incidences are on the rise, and many targeted companies have lost millions of dollars to cybercriminals in this way. The anonymity provided by crypto networks is partly to blame for the scourge. Most ransomware groups currently prefer that payments be made in privacy-centric tokens, a strategy that complicates the process of tracking down perpetrators. Here are some of the top ransomware removal and decryption tools you can use. But if in doubt, call in a professional. Kaspersky has about a dozen standalone ransomware removal tools that are designed to fix specific infections.
Ottawa hospital jobs
Yet the program is effective enough to recognize and decrypt a variety of ransomware file formats. Hazeem on November 21, at am. A reputable antivirus tool will remove ransomware from all your devices, including PC, Mac , Android , and iPhone. Please help me… My file infected by Virus Ransomware tipe. RakhniDecryptor can now decrypt the following ransomware families: BleepingComputer To decrypt files, first download RakhniDecryptor. Tom on October 12, at pm. My system Affected in. Aryan on September 23, at pm. Consider resetting the phone and restoring from a backup to ensure the ransomware has been completely purged. Matej on January 2, at pm. See all Performance articles. Aamir on February 10, at am. Filename changes: Encrypted files can be recognized by one of these file extensions:. Sukhendar on July 2, at pm. The integrity of the decrypted files is not guaranteed by Emsisoft tools, though.
Keep reading to learn how ransomware works, different types, and noteworthy examples of recent attacks.
Darko on December 20, at pm. Ransom message: After encryption is complete, the following screen will appear:. Ryuk Ryuk resembles the activities of older ransomware attacks like WannaCry , with the particularly nefarious characteristic of gaining as much access as possible before it encrypts anything. The ransomware assures the victims that they will receive a code to unlock their data if they pay. Our System has been encrypted by an phobos ransomware ending with. Ensure the backup is from a date prior to the ransomware attack to prevent re-infection. Learn how to prevent ransomware attacks. Later versions of the ransomware can also set the following image to the user's desktop:. Hello me to has been infected with the same virus if you find a solution please help me. I believe you are certainly the pioneer in your sector. Avast currently offers 30 free ransomware decryption tools for Microsoft Windows operating systems. Slim on August 27, at pm. You can use one of the following tools: ID Ransomware Ransomware Decryption Tools Once identified, you may know what common locations any remaining infection may occupy, the scope of the attack, and whether or not a decryption tool exists that would allow you to recover your files. After encrypting your files, Bart changes your desktop wallpaper to an image like the one below.

I congratulate, magnificent idea and it is duly