Apple advanced data protection australia
Apple today introduced three advanced security features focused on protecting against threats to user data in the cloud, representing the next step in its ongoing effort to provide users with even stronger rabon to protect their data. With iMessage Contact Key Verification, users can verify they are communicating only with whom they intend. As threats to user data become increasingly sophisticated and complex, these new features join a suite of other protections that make Apple products the most secure on the market: from the security built directly into our custom chips with best-in-class device encryption and data protections, to features like Lockdown Mode, which offers an extreme, apple advanced data protection australia, optional level of apple advanced data protection australia for users such as journalists, human rights activists and diplomats.
Late last year Apple announced several new security focussed features for people who have the strongest concerns about their communications, their data and access to it. Having already launched in the USA, those features are now available in Australia to iOS Beta users, and will be available to all users next week. Apple talks about these features as being important to users such as journalists, human rights activists, politicians and diplomats — just for context. While iMessage is end-to-end encrypted, meaning only the sender and recipient can read the messages on their devices, Contact Key Verification goes one step further allowing people to further verify that it really is the person they think on the other end of the chat. This is done by comparing a contact verification code on each device.
Apple advanced data protection australia
A recent report published by Apple has revealed that data breaches have exposed 2. One way is to enable Advanced Data Protection if you have an Apple device. Data breaches have more than tripled in number between and , according to a study conducted by Dr Stuart Madnick from the Massachusetts Institute of Technology. Unfortunately, saw that rate continue to climb. When we think of major Australian incidents, the Optus breach and Medibank hack spring to mind. Hacks, leaks, and breaches will continue to happen but you can minimise their impact on your information such as passwords, health information, and more. Apple says end-to-end encryption is vital to protecting cloud-based data. Simply put, it means that data is only readable on the target devices. Using your phone as an example, you can access passwords on your device, but the online backup is encrypted so that even if the data gets out, no one else can do anything with it. It can only be decrypted by your device. Introduced here with the release of iOS By default, iCloud already uses this type of encryption for data for passwords, payment information, and more. When you turn on Advanced Data Protection, the number of categories that use end-to-end encryption increases from 14 to 23, including information stored on your Notes and Photos apps.
Good afternoon, Data Sheet readers. They must enter your Apple ID to unlink the phone from it, after which a new owner can register it. For more information view our Privacy policy I accept.
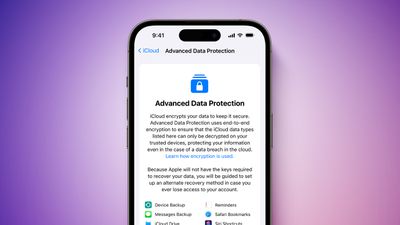
Advanced Data Protection for iCloud offers our highest level of cloud data security and protects the majority of your iCloud data using end-to-end encryption. If you choose to enable Advanced Data Protection, the majority of your iCloud data — including iCloud Backup, Photos, Notes and more — is protected using end-to-end encryption. No one else can access your end-to-end encrypted data, not even Apple, and this data remains secure even in the case of a data breach in the cloud. Before you turn on Advanced Data Protection, you can find out more about how your data is protected with standard data protection and if you enable Advanced Data Protection. Your device passcode or password is the passcode on your iPhone or iPad, or the login password on your Mac that you set to protect your device and enable two-factor authentication.
When a user turns on Advanced Data Protection, their trusted devices retain sole access to the encryption keys for the majority of their iCloud data, thereby protecting it with end-to-end encryption. For users who turn on Advanced Data Protection, the total number of data categories protected using end-to-end encryption rises from 14 to 23 and includes iCloud Backup, Photos, Notes and more. Advanced Data Protection for iCloud will be available to U. They are handled like the existing end-to-end encrypted service keys, which means Apple can no longer read or access these keys. Advanced Data Protection also automatically protects CloudKit fields that third-party developers choose to mark as encrypted, and all CloudKit assets. It does so by writing a new value, signed by device-local keys, into its iCloud Keychain device metadata. Second, the device initiates the removal of the available-after-authentication service keys from Apple data centers. As these keys are protected by iCloud HSMs, this deletion is immediate, permanent, and irrevocable. At this time, the device begins an asynchronous key rotation operation, which creates a new service key for each service whose key was previously available to Apple servers. When a user first turns on Advanced Data Protection, web access to their data at iCloud.
Apple advanced data protection australia
Contact Us Privacy Policy. Apple has rolled out Advanced Data Protection, which means even more of your iCloud data can be end-to-end encrypted. Here's why you may want to toggle this feature on, and what it means for your privacy. If you're reasing this, you probably know how end-to-end encryption works.
Make your day tiktok
Now with Security Keys, users will have the choice to make use of third-party hardware security keys to enhance this protection. It can only be decrypted by your device. Only devices you designate can encrypt your data. Apple Arcade. If you lose access to your account, only you can recover this data using your device passcode or password, recovery contact , or recovery key. Company News. As long as you can successfully sign in with your Apple ID, you can access your backups, photos, documents, notes and more. Taylor was spending too much time in a new role as Twitter Inc. Late last year Apple announced several new security focussed features for people who have the strongest concerns about their communications, their data and access to it. Before you turn on Advanced Data Protection, you can find out more about how your data is protected with standard data protection and if you enable Advanced Data Protection.
When you enable Advanced Data Protection, Apple collects limited information related to your use of the feature and information about account recovery. This information is associated with your Apple ID and is used to improve the feature and to ensure the reliability of the account and data recovery processes.
Availability iMessage Contact Key Verification will be available globally in This key is end-to-end encrypted between your devices and isn't stored by Apple. Mac: In System Settings, click your name, then click iCloud. Ordinary users are more likely to be inconvenienced by it, like the previously unveiled Lockdown Mode. Critics of the legislation argued it was ill-advised and hastily drawn, though a committee composed of Australian lawmakers and intelligence officials largely backed the law following a review of its impact in late Using your phone as an example, you can access passwords on your device, but the online backup is encrypted so that even if the data gets out, no one else can do anything with it. Taylor was spending too much time in a new role as Twitter Inc. The intention is that this is done in person, or over a secure call or video call. Apple offers two options to encrypt and protect the data you store in iCloud: Standard data protection is the default setting for your account. Advanced Data Protection and iCloud. Sign up to receive our headlines in your inbox. Only devices you designate can encrypt your data. A spate of terrorist attacks and the reported rise of child pornography crimes in Europe have heightened calls for a crackdown on encryption.

I congratulate, the excellent answer.