4chan soc
I had a couple but they disappeared for some reason Motherless is a moral free file host where anything legal is hosted forever!
You can also set up your profile. Get it now! Verify Your Email. In order to vote, comment or post rants, you need to confirm your email address. You should have received a welcome email with a confirm link when you signed up.
4chan soc
.
Top 10 Friend Sites.
.
Please purchase an Enhanced Subscription to continue reading. To continue, please log in, or sign up for a new account. We offer one free story view per month. If you register for an account, you will get two additional story views. After those three total views, we ask that you support us with a subscription. A subscription to our digital content is so much more than just access to our valuable content. Thank you very much! Please log in, or sign up for a new account to continue reading. Thank you for visiting the Daily Journal.
4chan soc
Learn how security operations center teams rapidly detect, prioritize, and triage potential cyberattacks. The SOC team, which may be onsite or outsourced, monitors identities, endpoints, servers, databases, network applications, websites, and other systems to uncover potential cyberattacks in real time. It also does proactive security work by using the latest threat intelligence to stay current on threat groups and infrastructure and identify and address system or process vulnerabilities before attackers exploit them. Most SOCs operate around the clock seven days a week, and large organizations that span multiple countries may also depend on a global security operations center GSOC to stay on top of worldwide security threats and coordinate detection and response among several local SOCs. SOC team members take on the following functions to help prevent, respond, and recover from attacks. To eliminate blind spots and gaps in coverage, the SOC needs visibility into the assets that it protects and insight into the tools it uses to defend the organization. This means accounting for all the databases, cloud services, identities, applications, and endpoints across on-premises and multiple clouds. The team also keeps track of all the security solutions used in the organization, such as firewalls, anti-malware, anti-ransomware, and monitoring software.
Lunden roberts
Quote Strike Insert Image url Insert. Your comment must be between 6 and characters. You should have received a welcome email with a confirm link when you signed up. Show More. Relevance Date. Motherless is a moral free file host where anything legal is hosted forever! If you want to blame someone for the content on this site, blame the freaks of the world - not us. Top 10 Friend Sites. Weird Galleries. Practically, the problem would be with the delay caused due to running this loop and very small times arriving towards the end of a very very large array. FYI we never show your email to other members. We use cookies to optimize our site and give you the best experience.
One of the most notorious places on the internet gets the biography it deserves in this fascinating documentary. Deputy Entertainment Editor.
Top 10 Friend Sites. FYI we never show your email to other members. Mobile Desktop. Switch to Old Version. How to Survive a Gangbang anonymous Your rant must be between 6 and 5, characters. Your comment must be between 6 and characters. Build your custom avatar. Post your own. Practically, the problem would be with the delay caused due to running this loop and very small times arriving towards the end of a very very large array. Join Motherless. I had a couple but they disappeared for some reason You should have received a welcome email with a confirm link when you signed up.

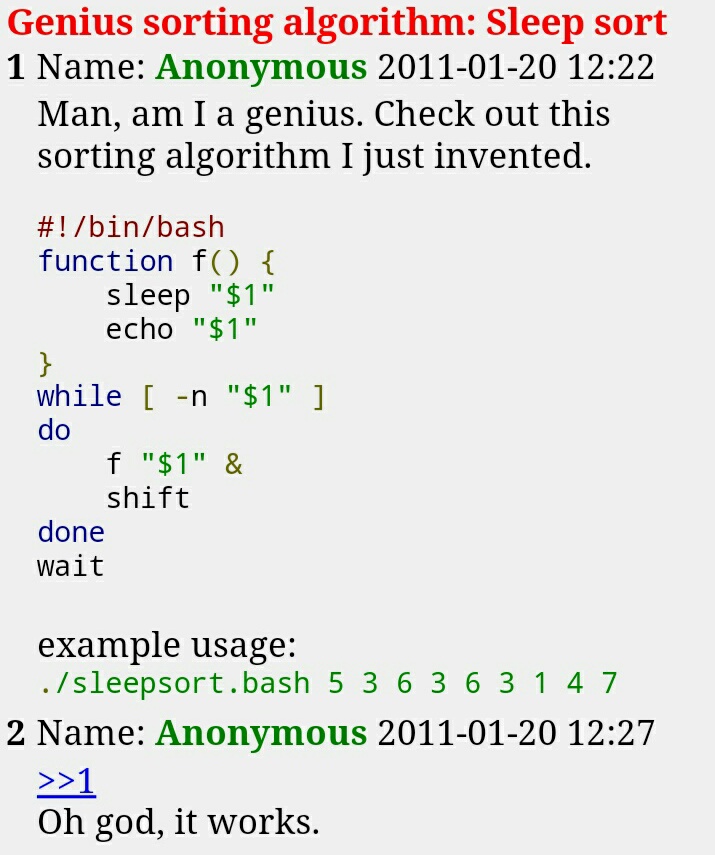
It agree, it is a remarkable piece
I consider, that you are not right. I am assured. Let's discuss.